Find the vulnerabilities that matter to you right now
CSTOOL.io allows you to list vulnerabilities for the products that you are using. It highlights vulnerabilities that have known exploits or that are currently being discussed in the news. To do that, CSTOOL.io consists of a collection of services:
To access the individual projects and source code see the links below. To start using the service simply click on the button above.
Overview of features
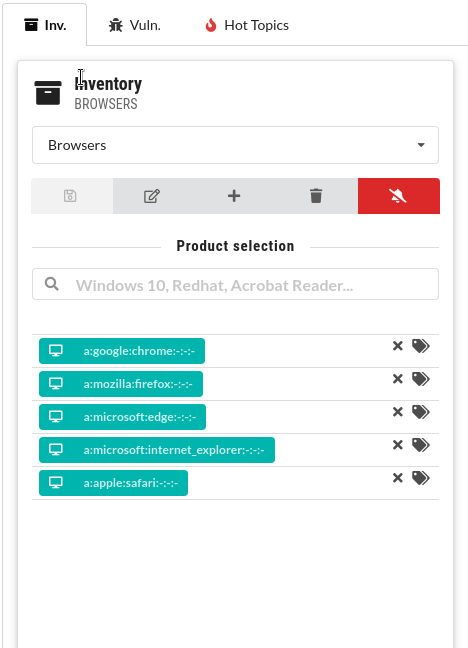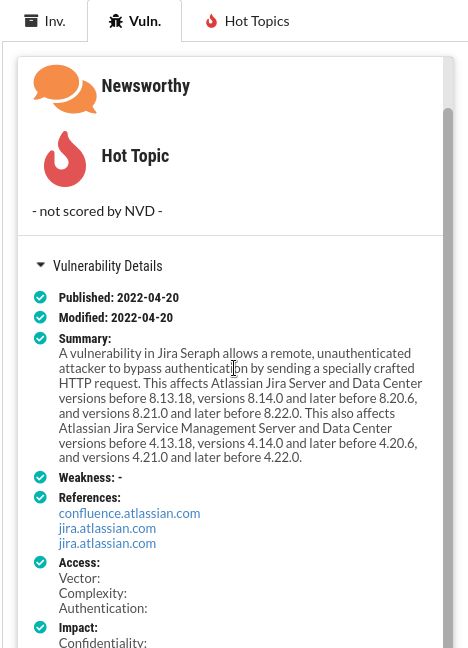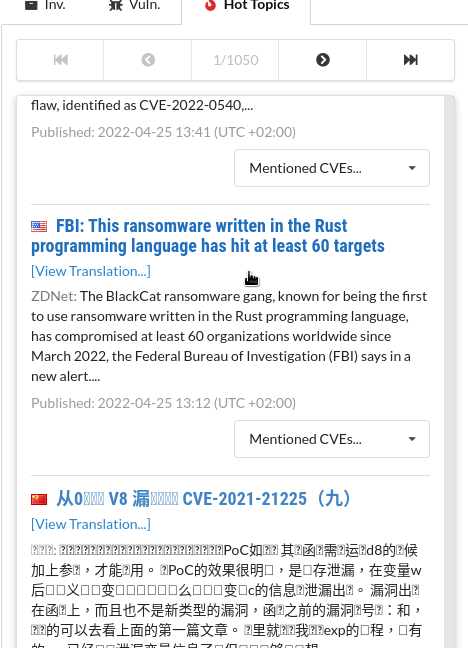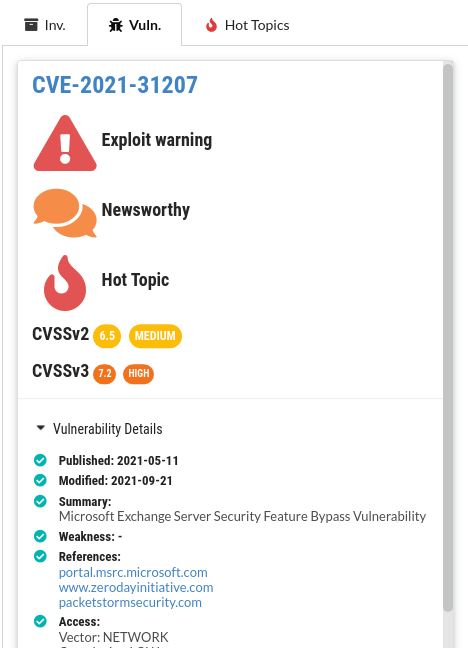
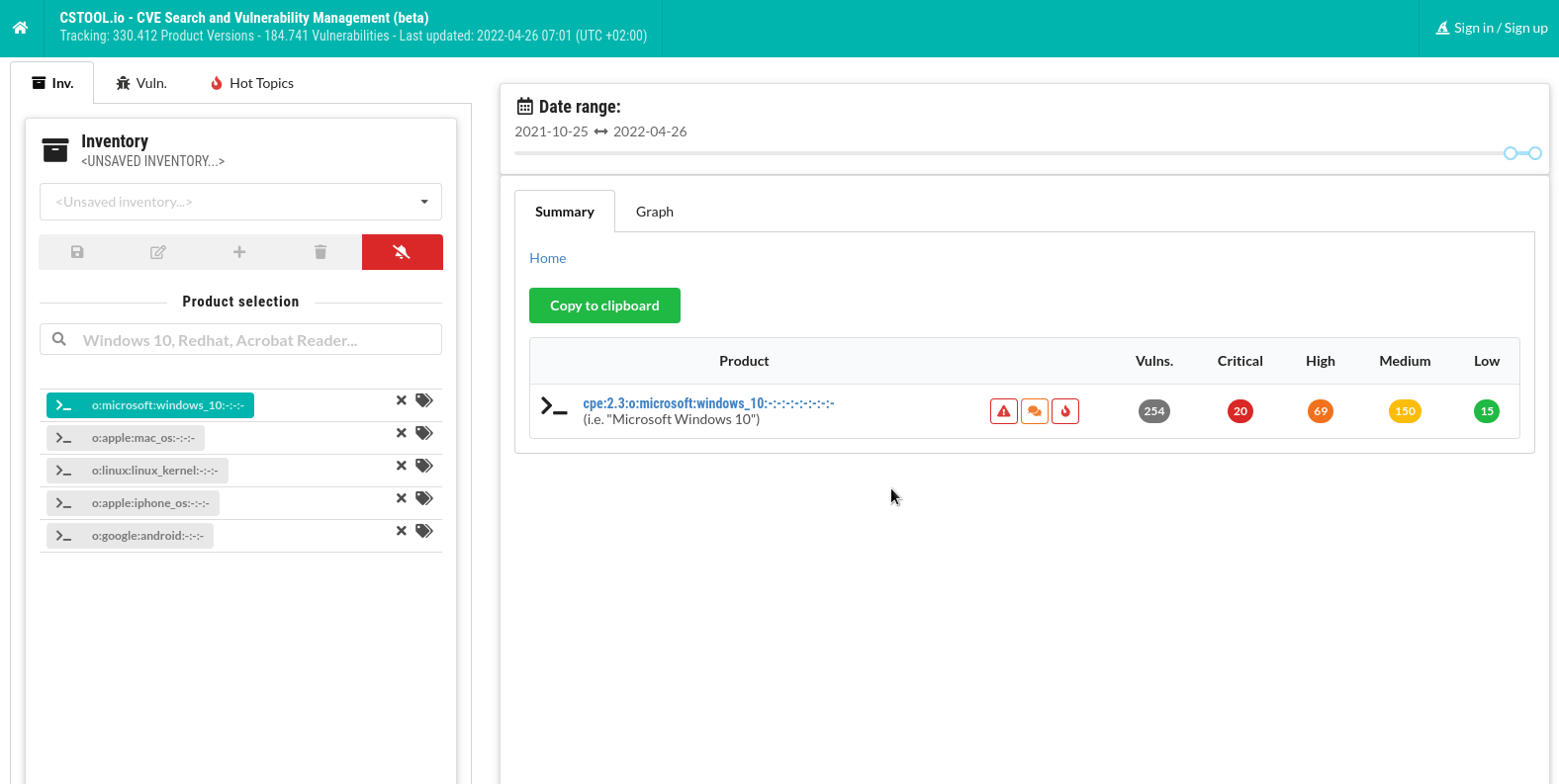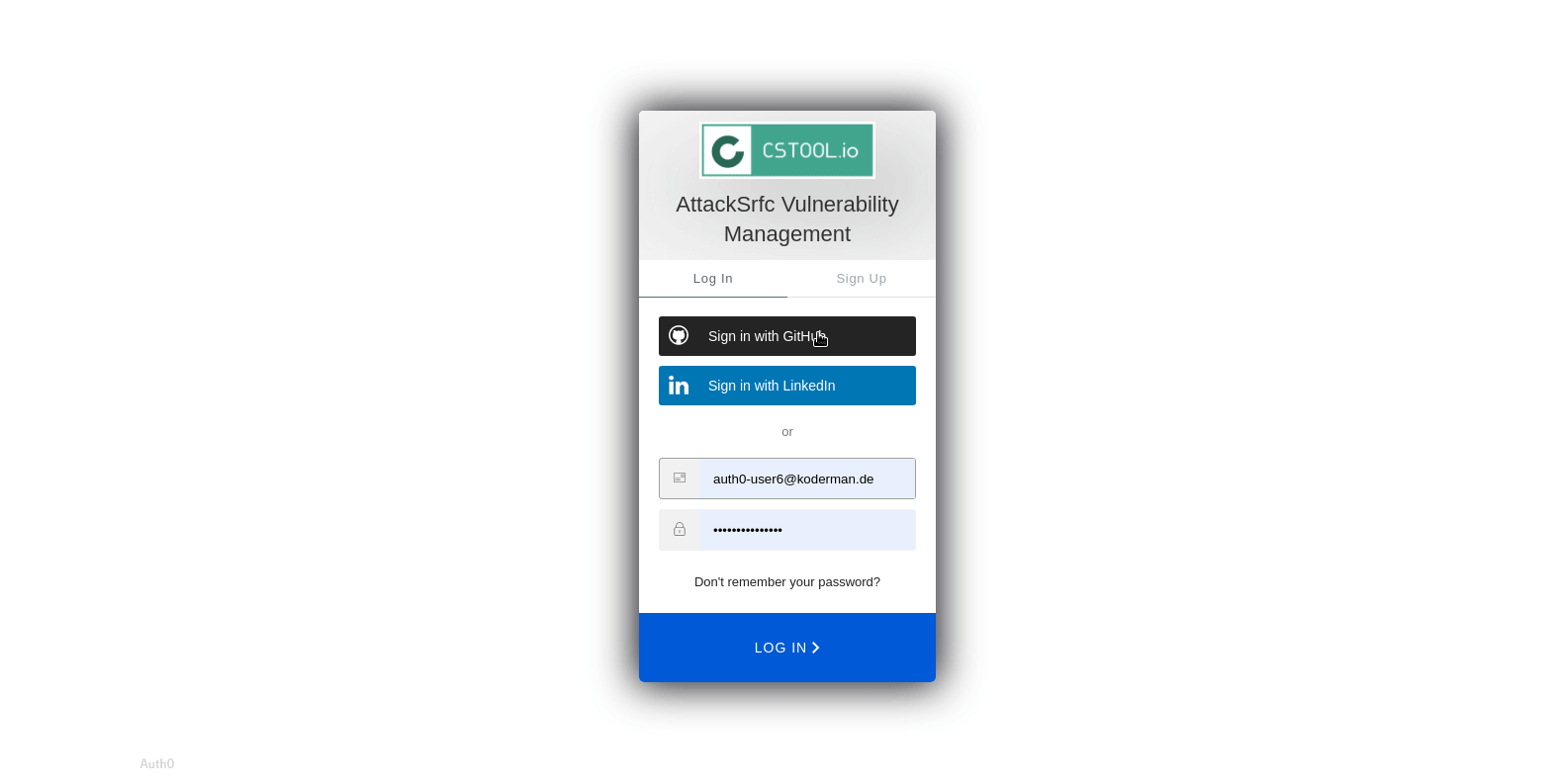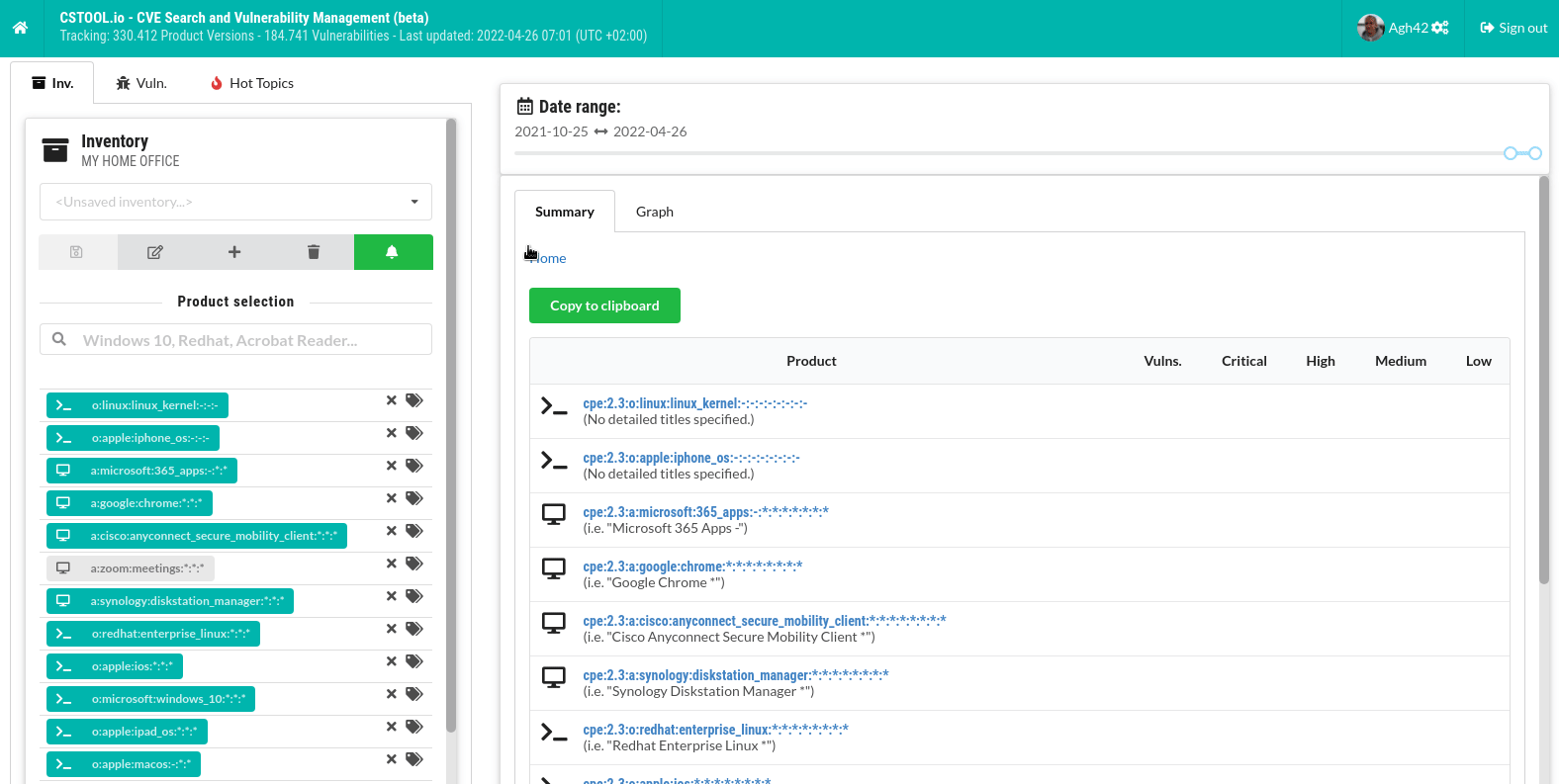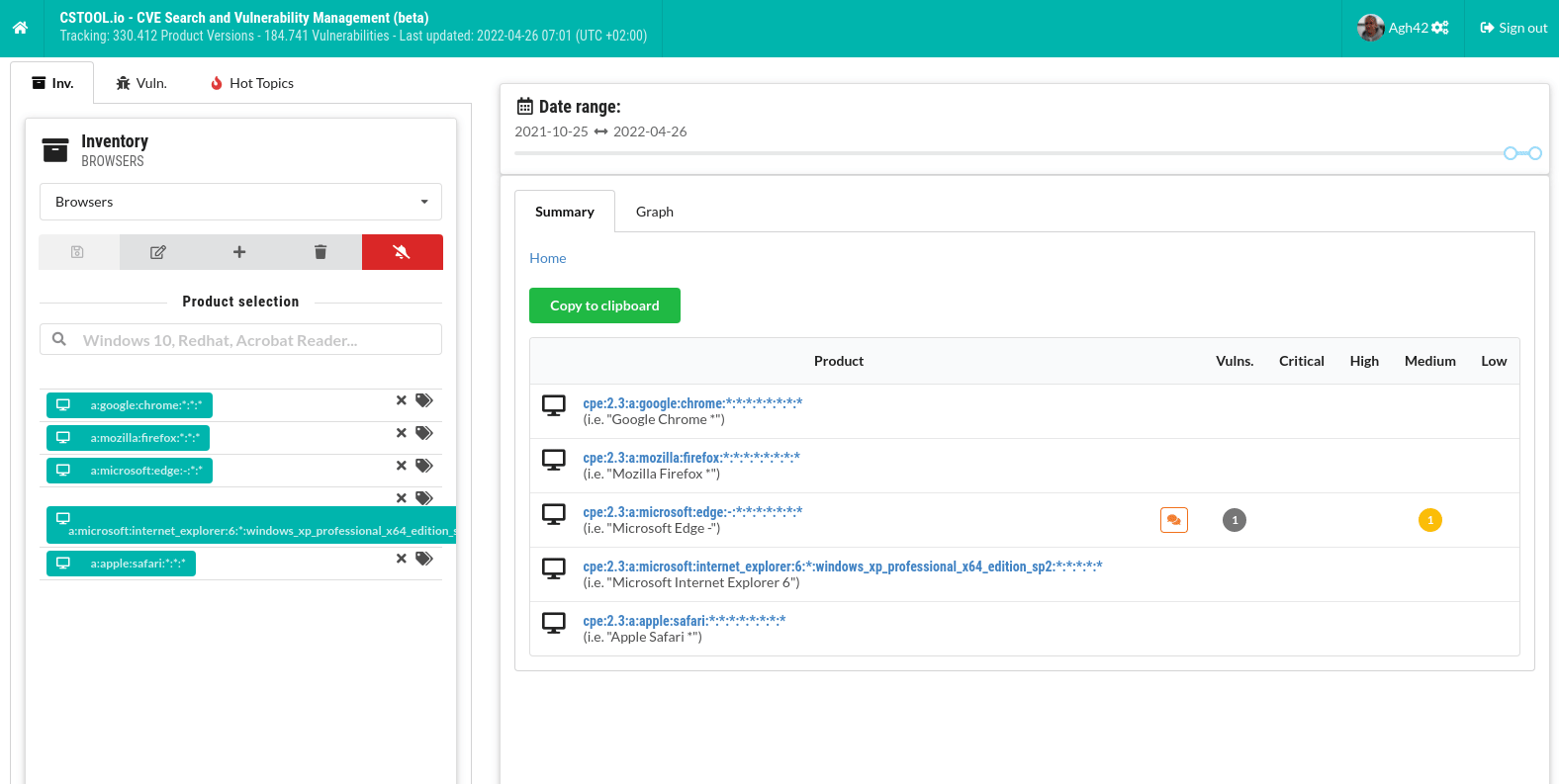
You can search for vulnerabilities and create different inventories of hardware and software:
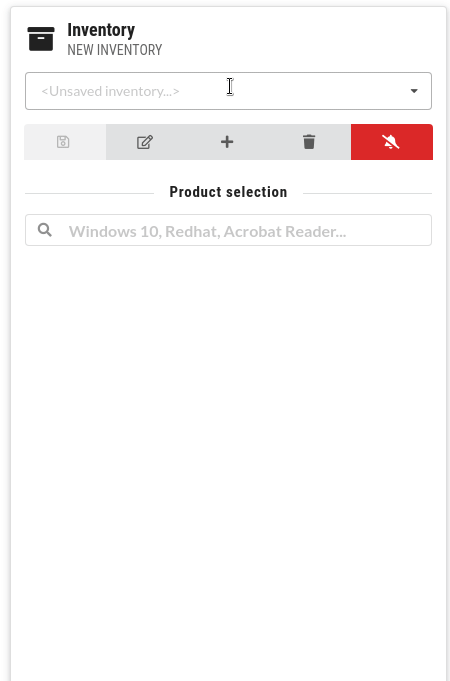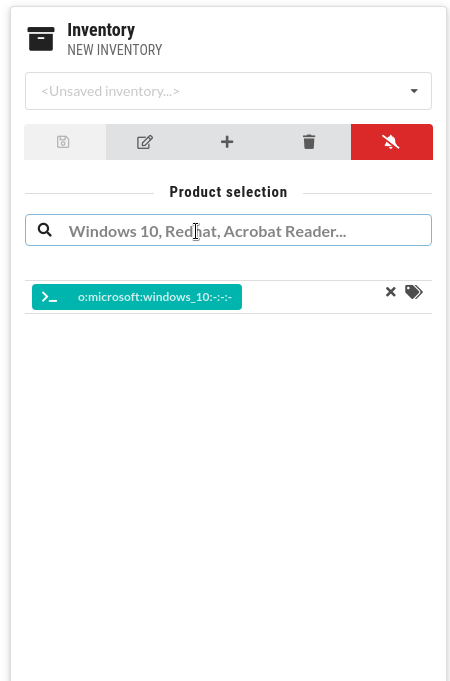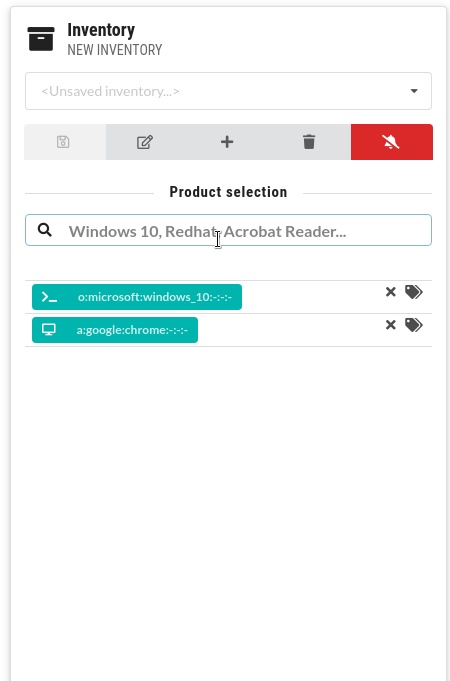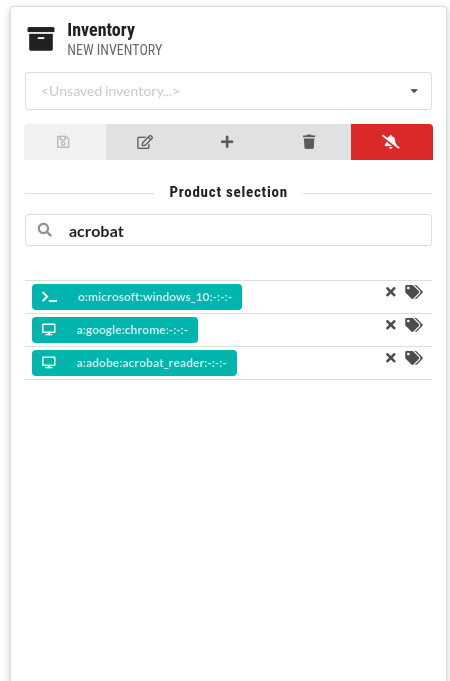
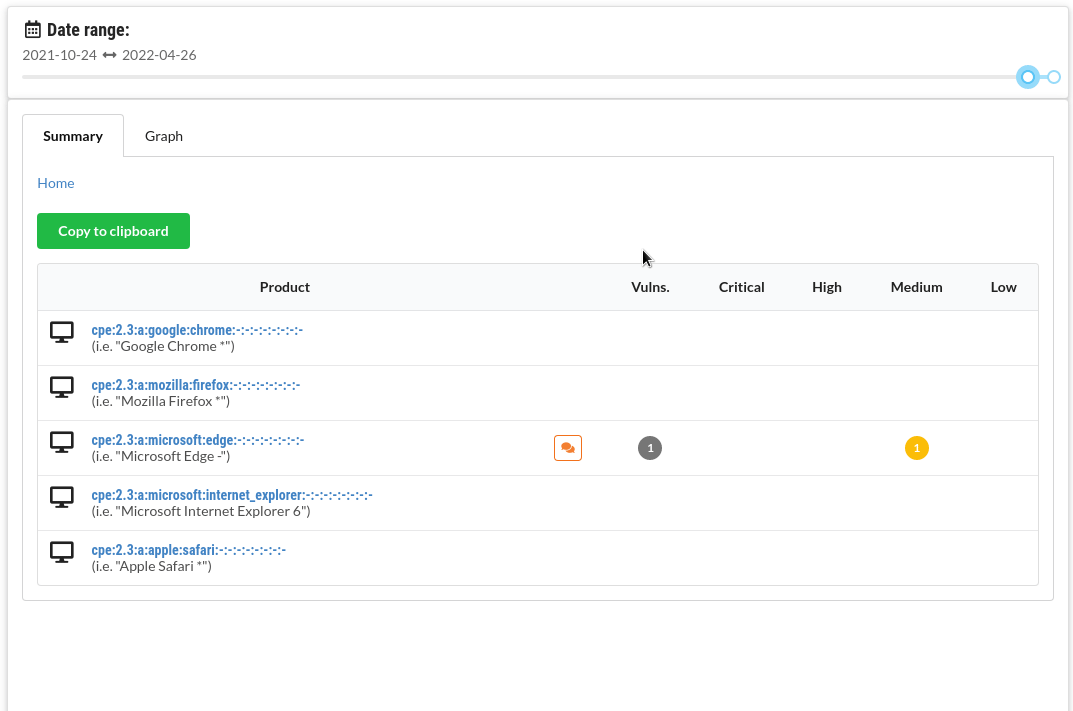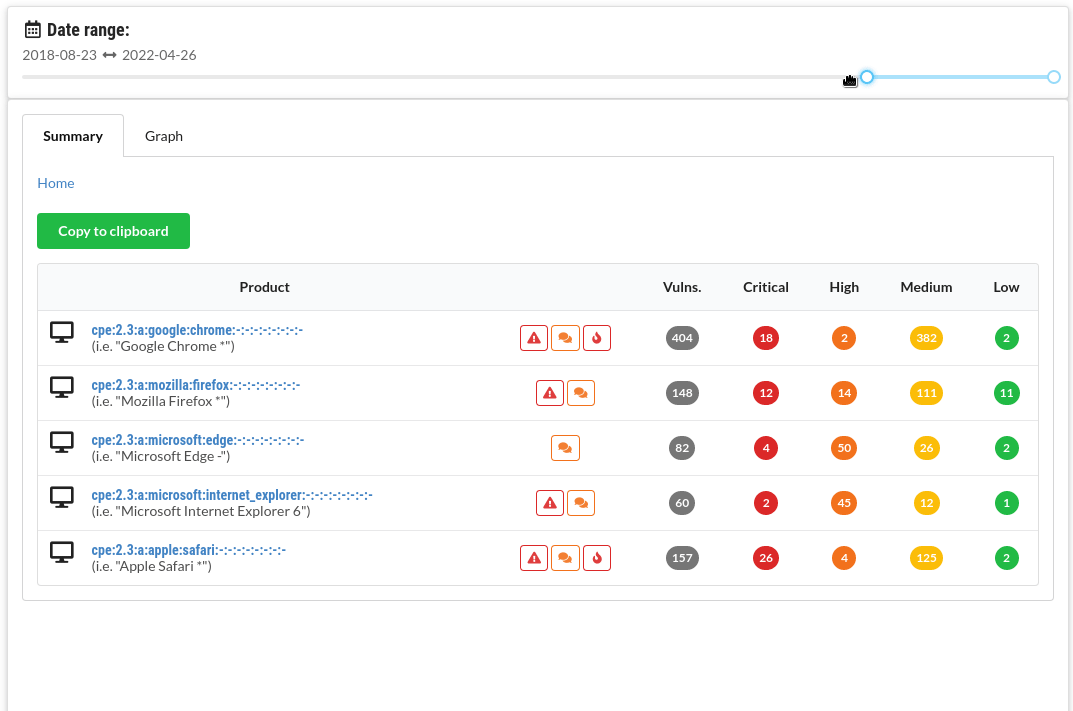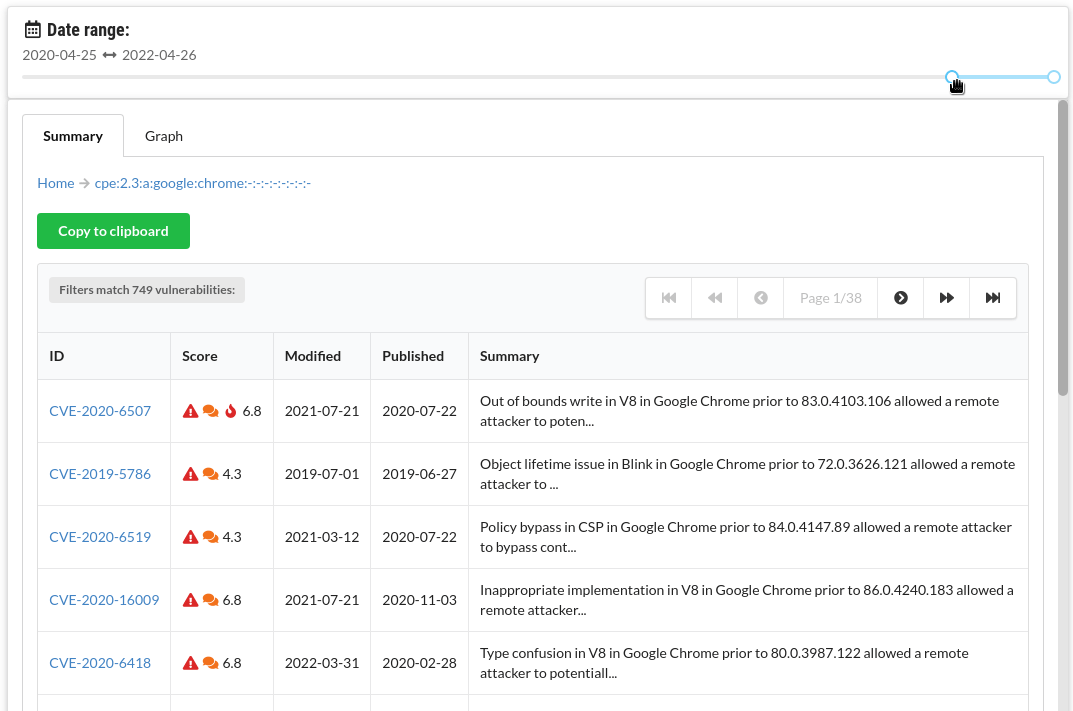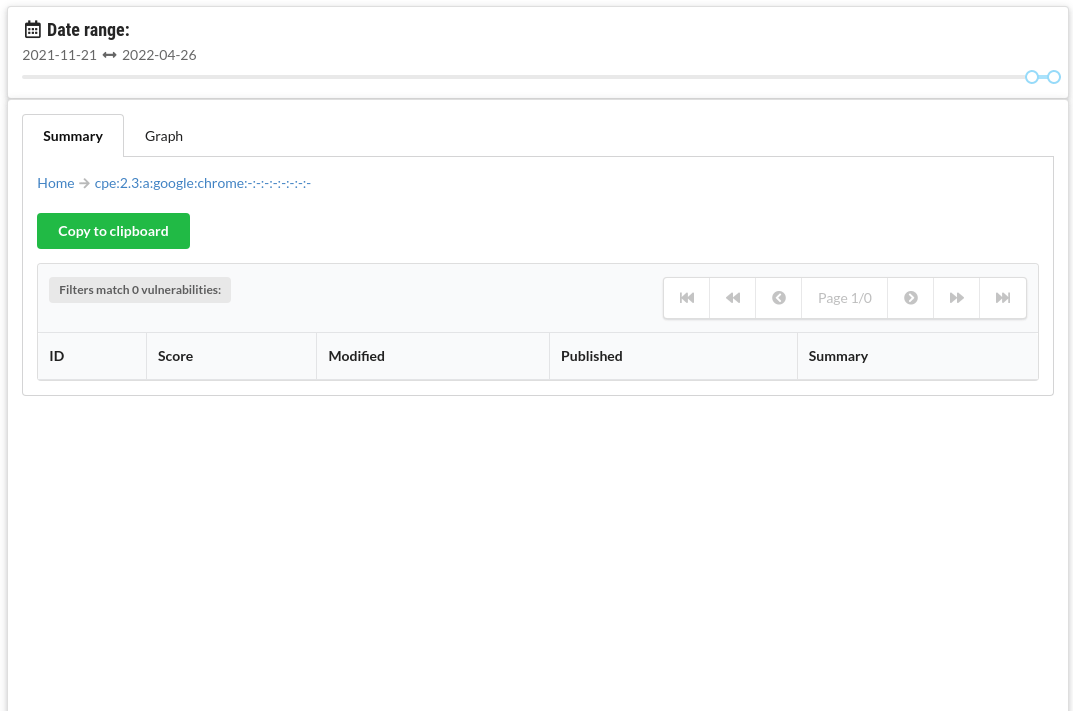
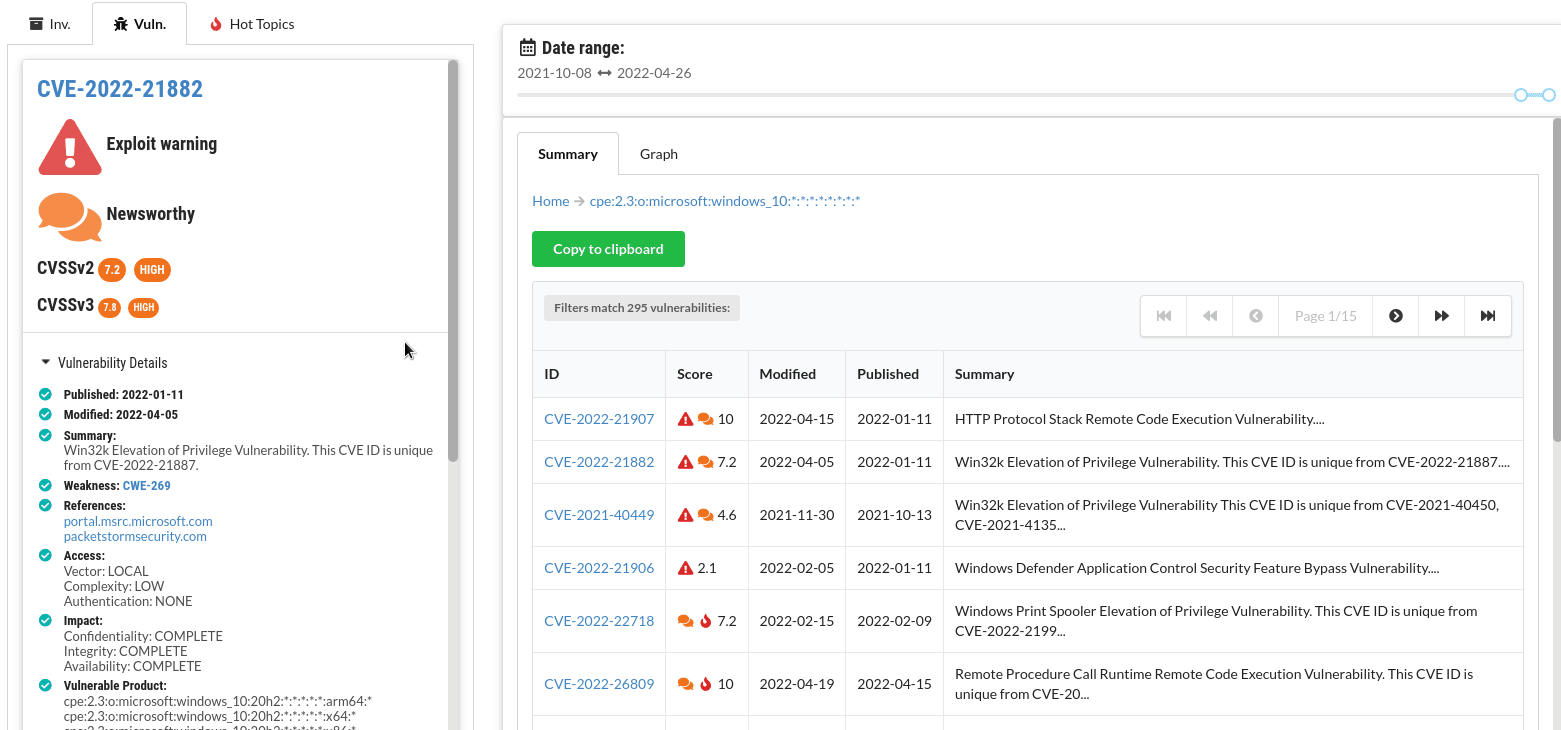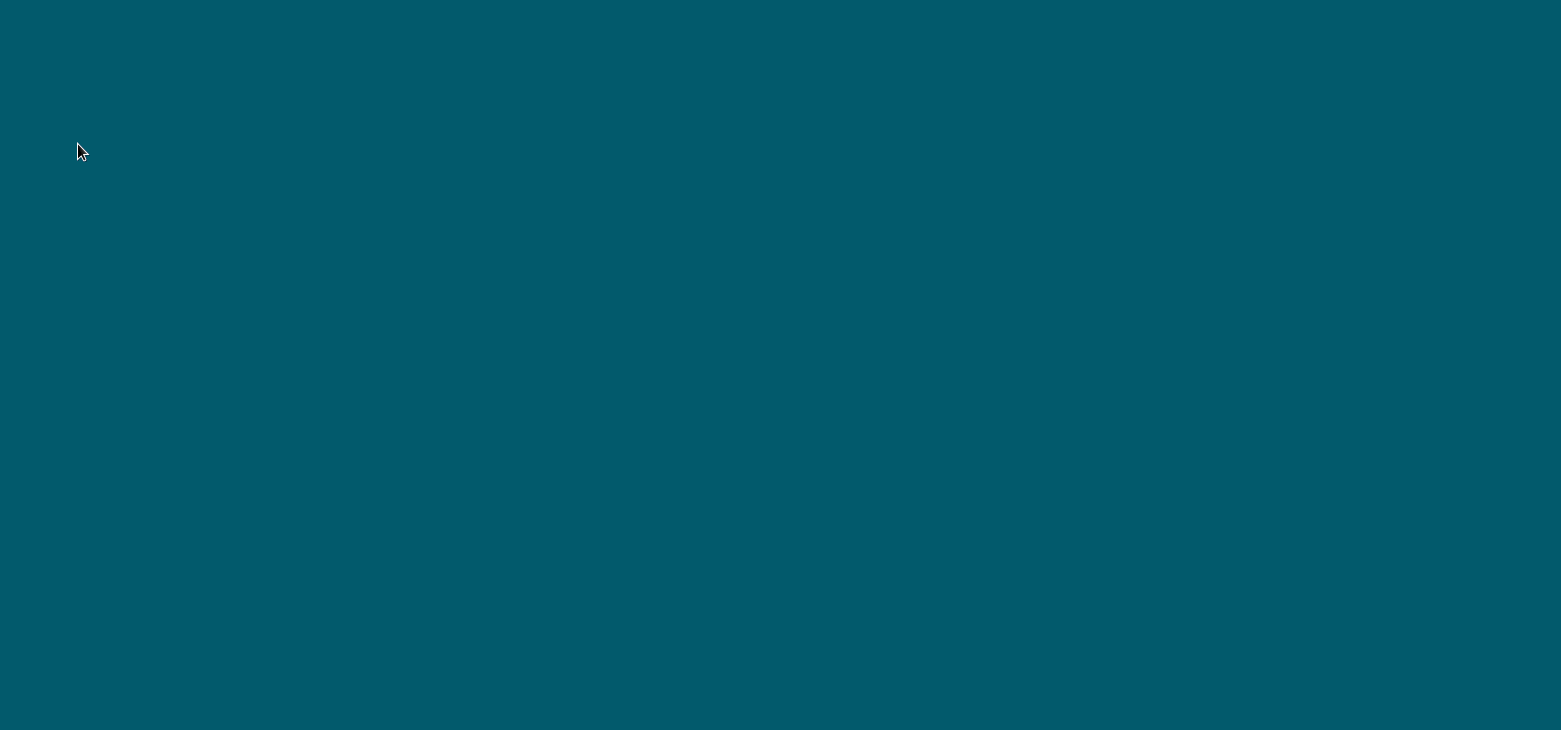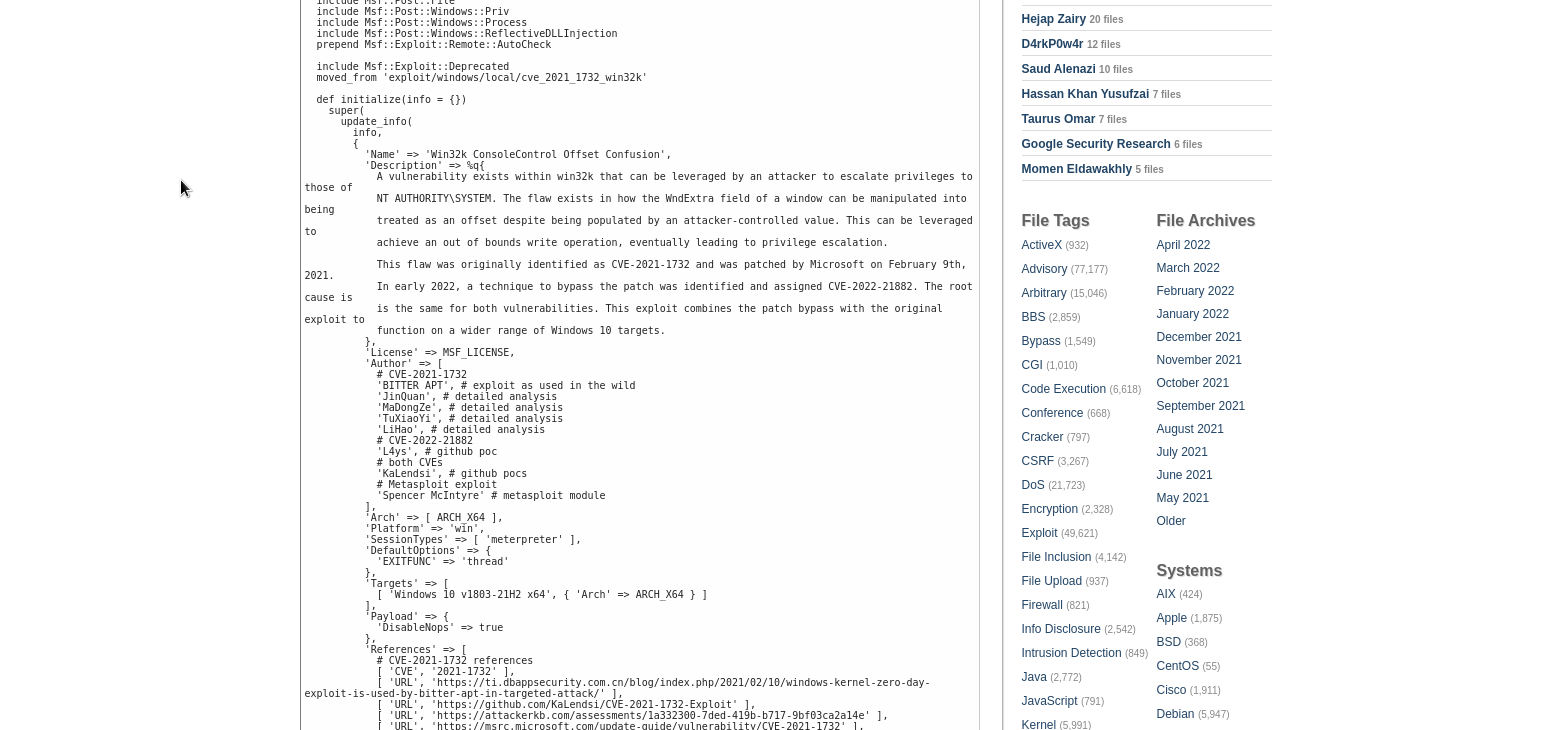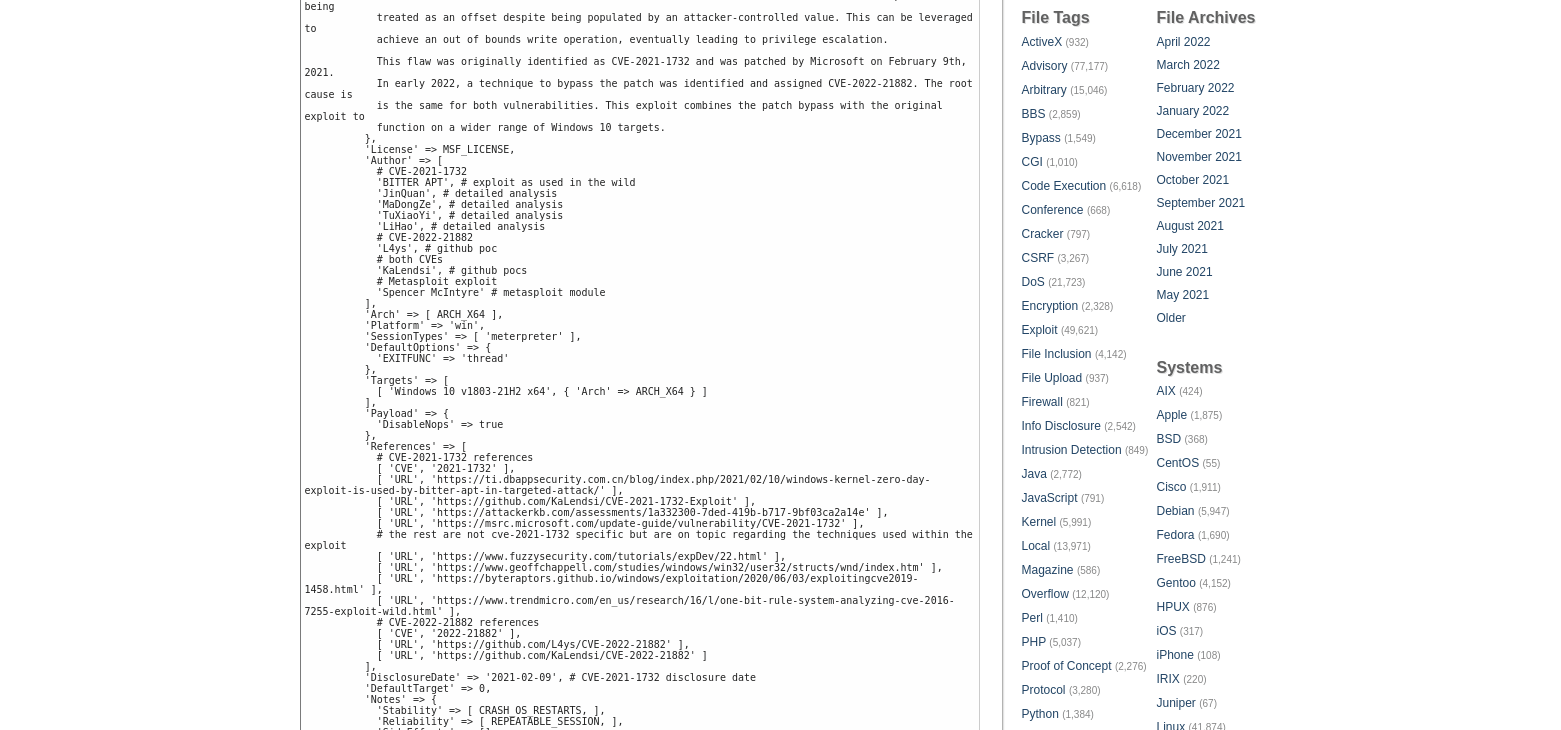
Time ranges
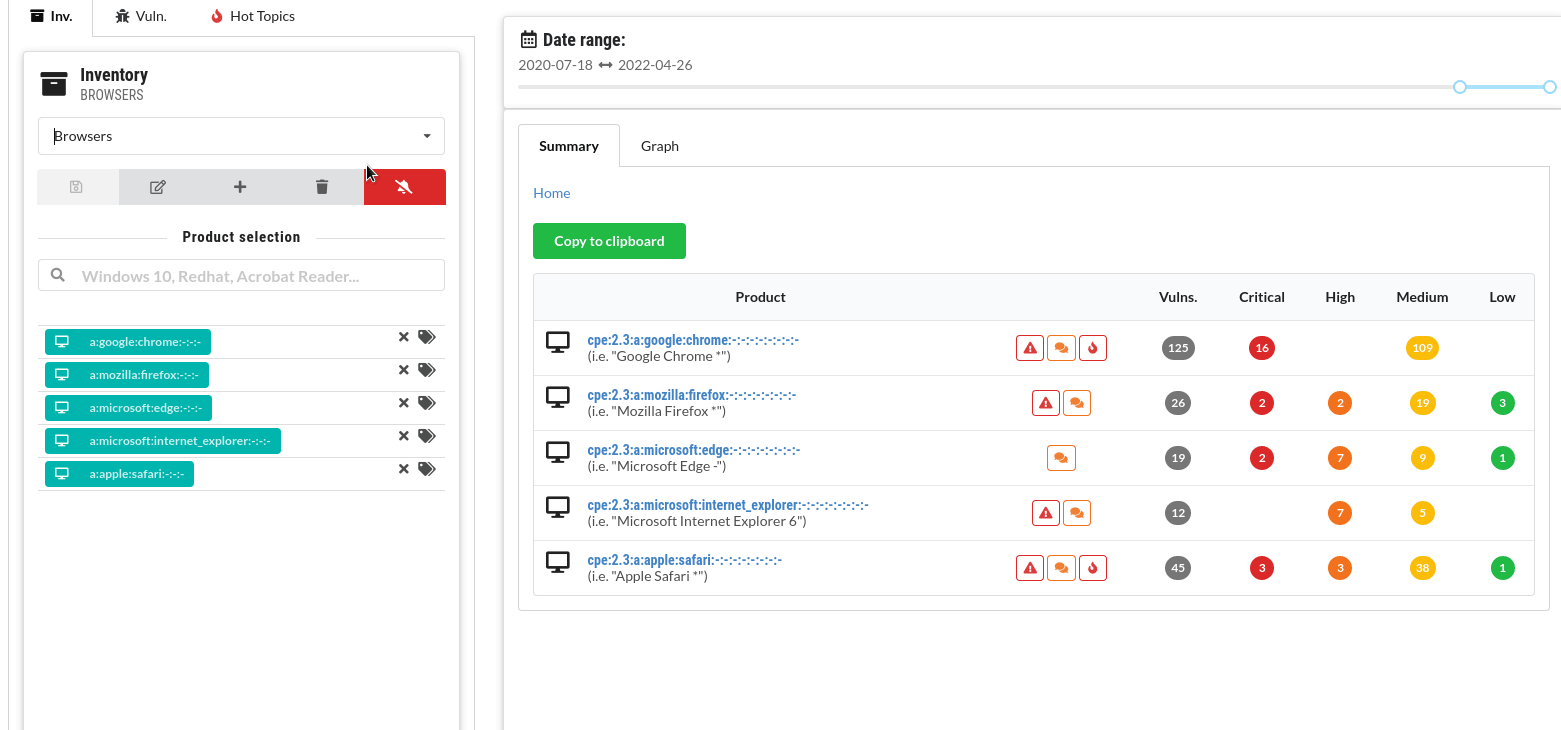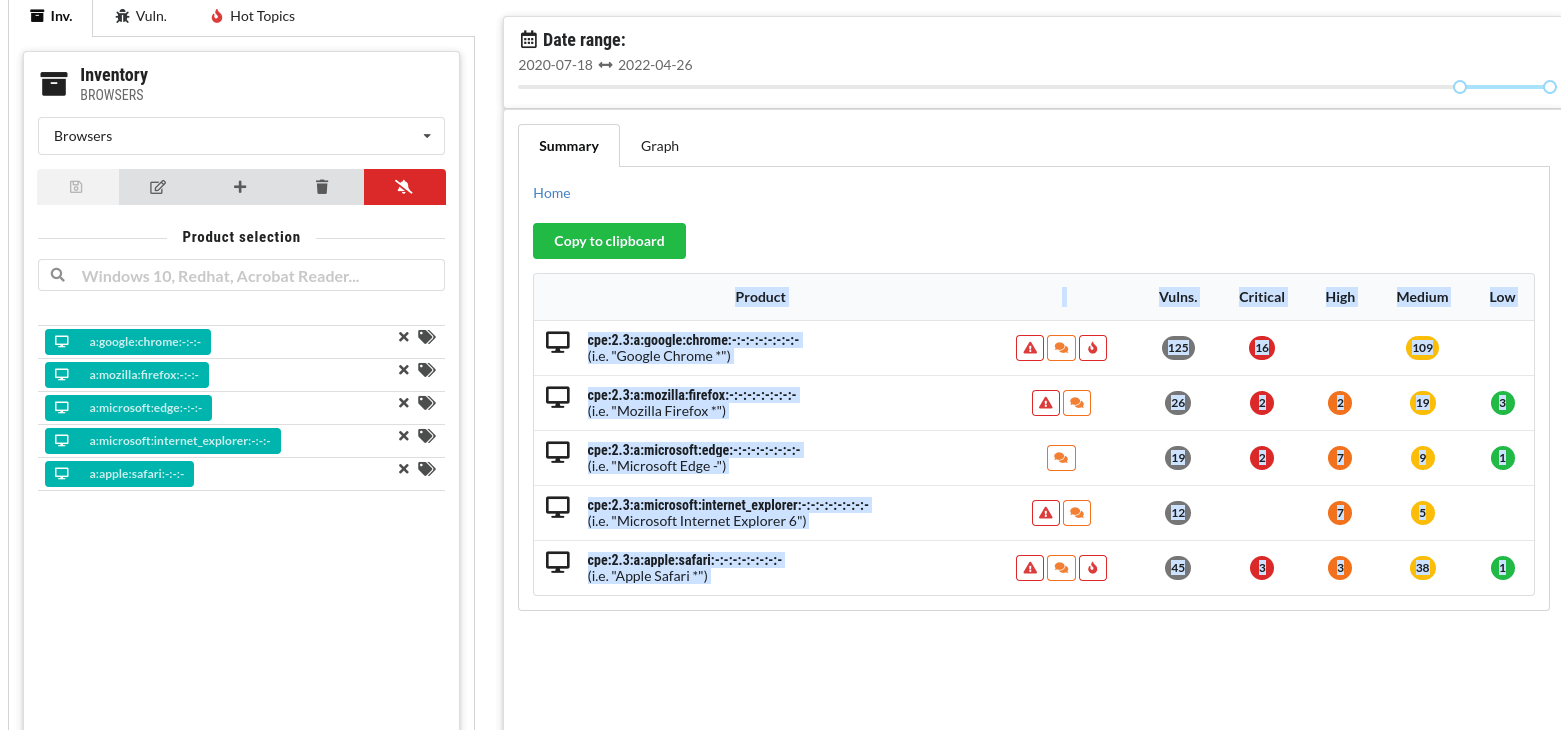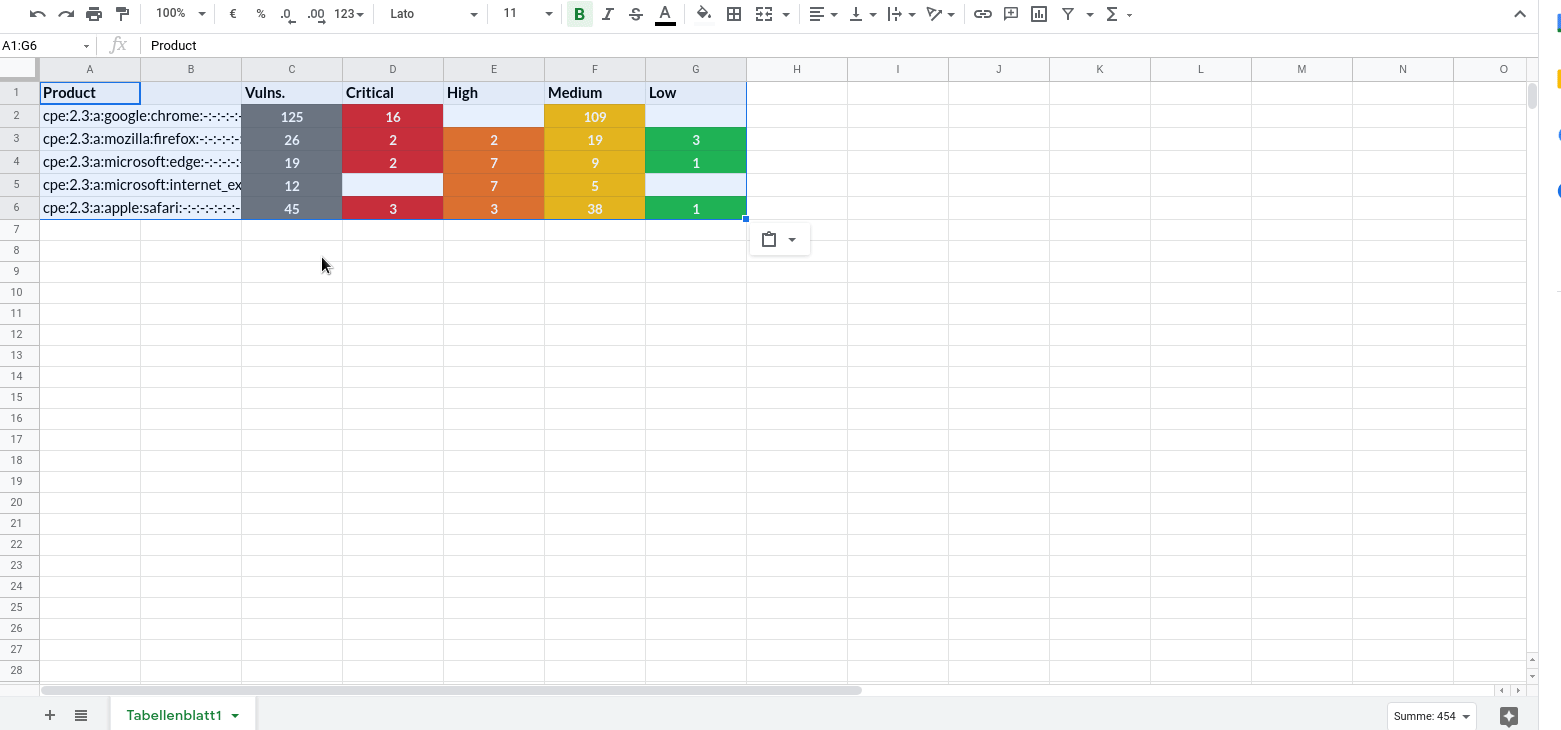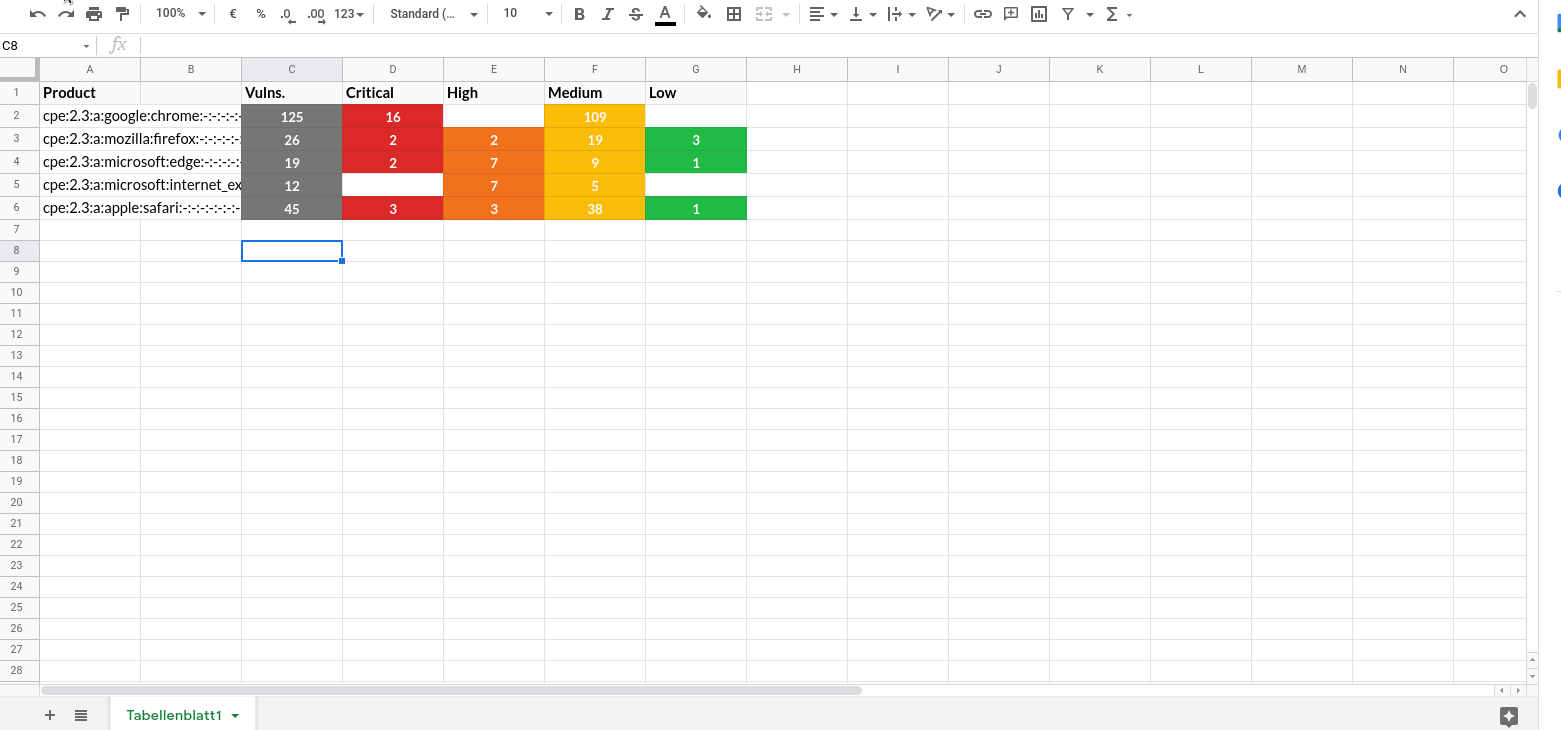
Compare vulnerabilities for a number of products in a selected time range. For instance, compare different browsers:
Graph view
Find out which other products are affected by the combined vulnerabilities of one product.
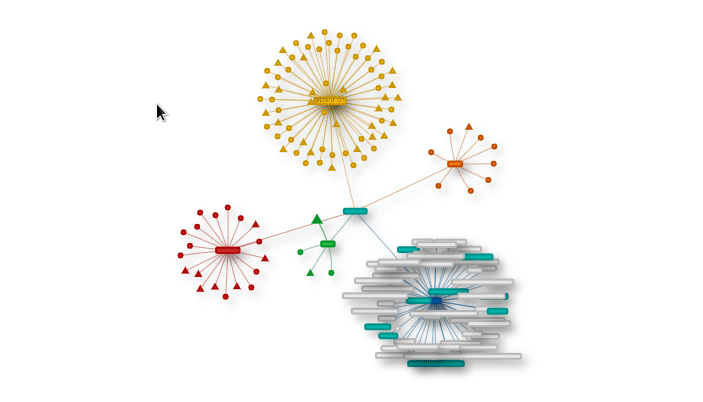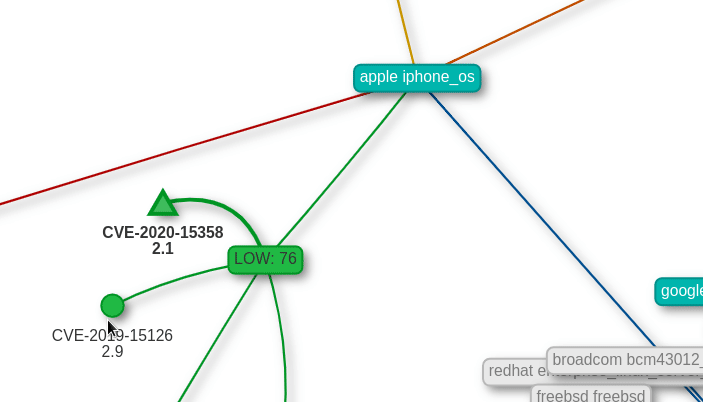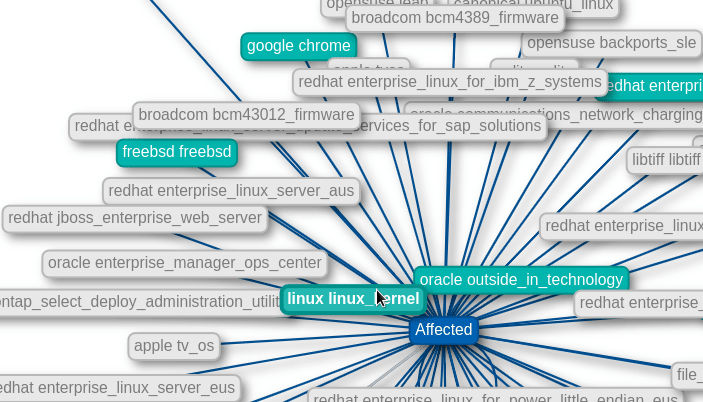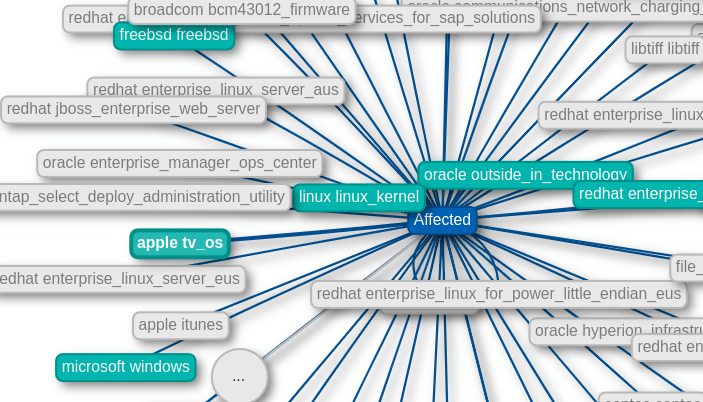
Highlighted items
If any vulnerabilities have known exploits or were mentioned in the news, these are highlighted in the summary.
API example: Search for the latest cybersecurity news
CSTOOL.io correlates CVEs and cybersecurity news articles.
I.e. to search for the most up-to-date news (hot topics) that mention CVEs:
Request more / older articles:
See below for more API examples.

Correlated cybersecurity news search
CSTOOL.io constantly monitors worldwide news and links the articles to mentioned vulnerabilities. Find out which vulnerabilities are currently being discussed or actively used in attacks.
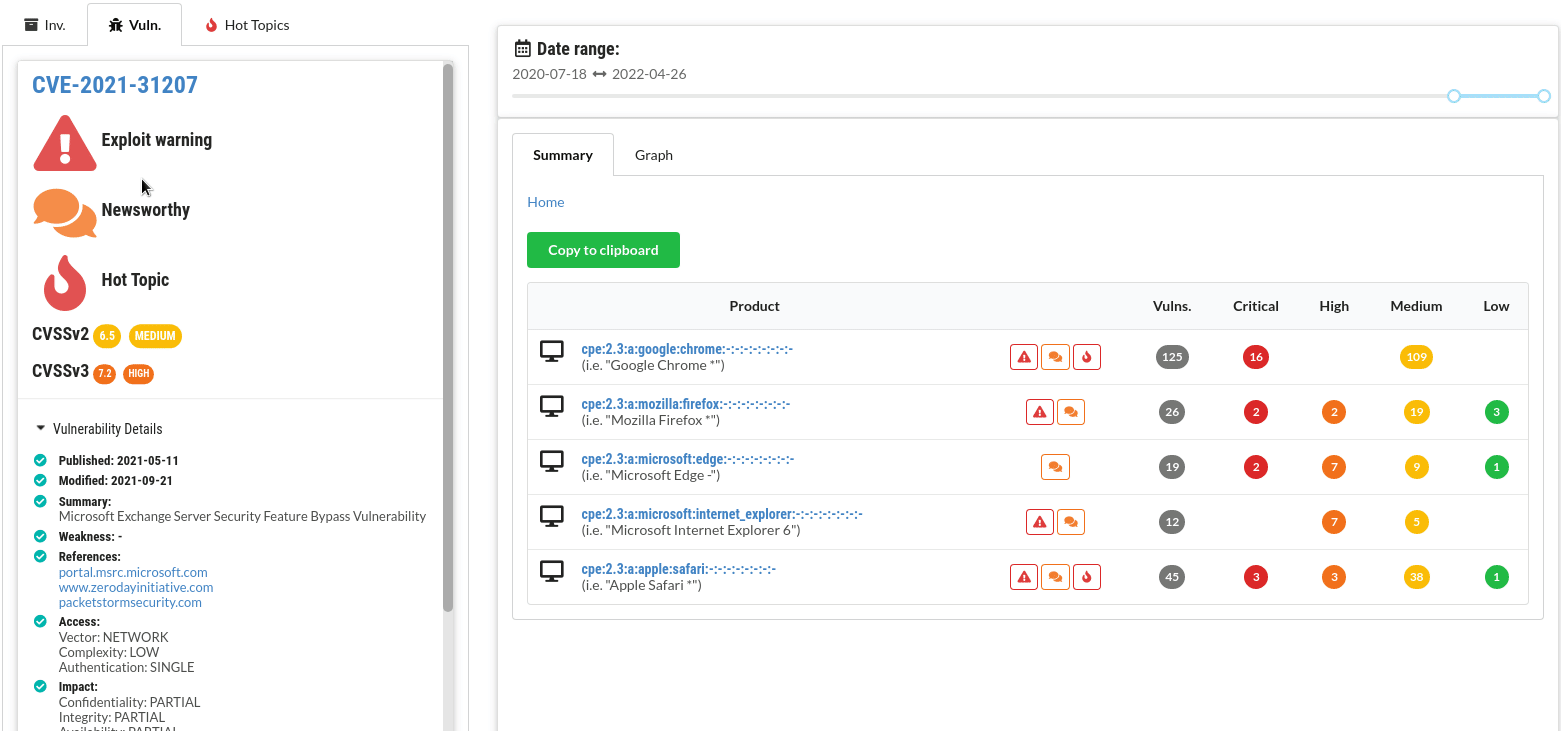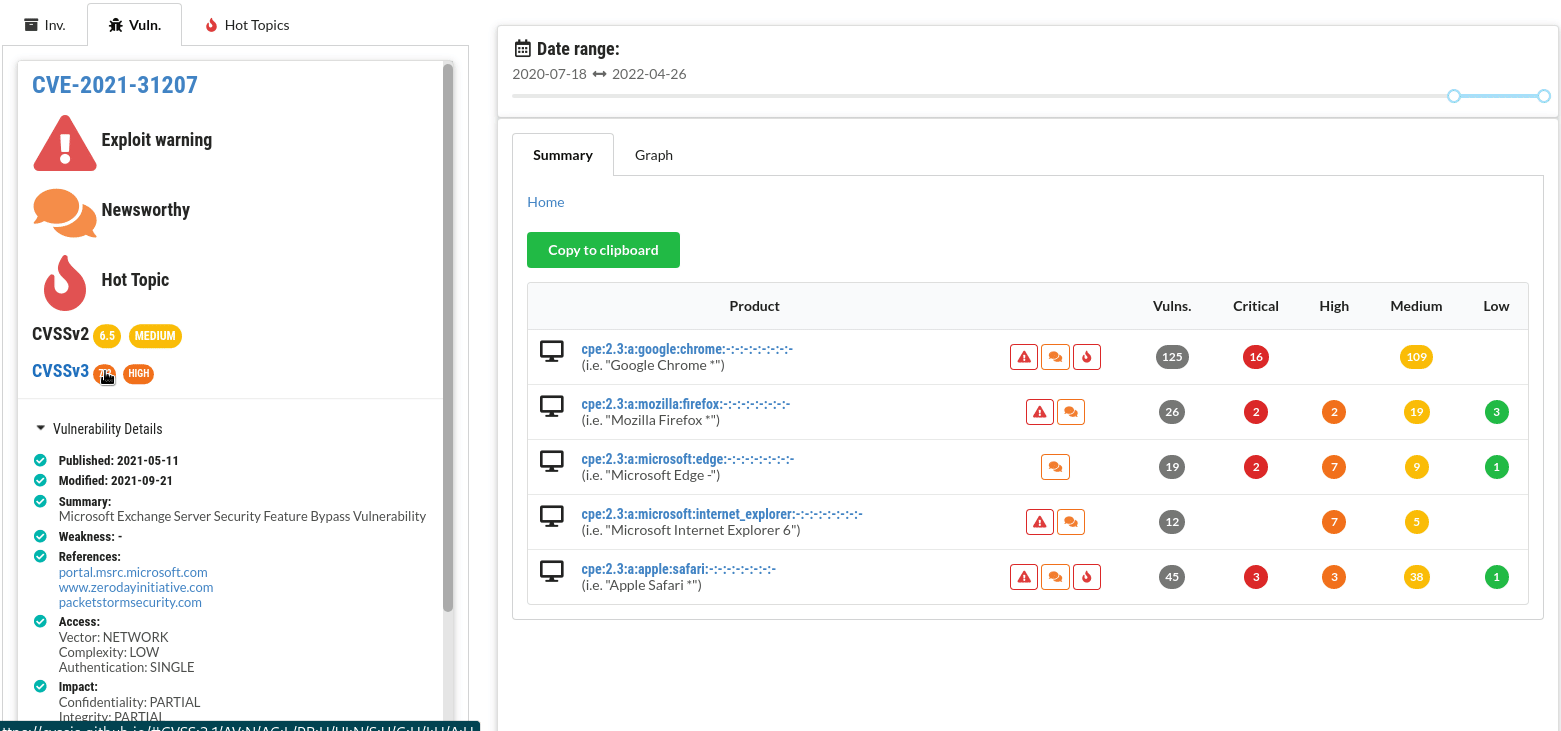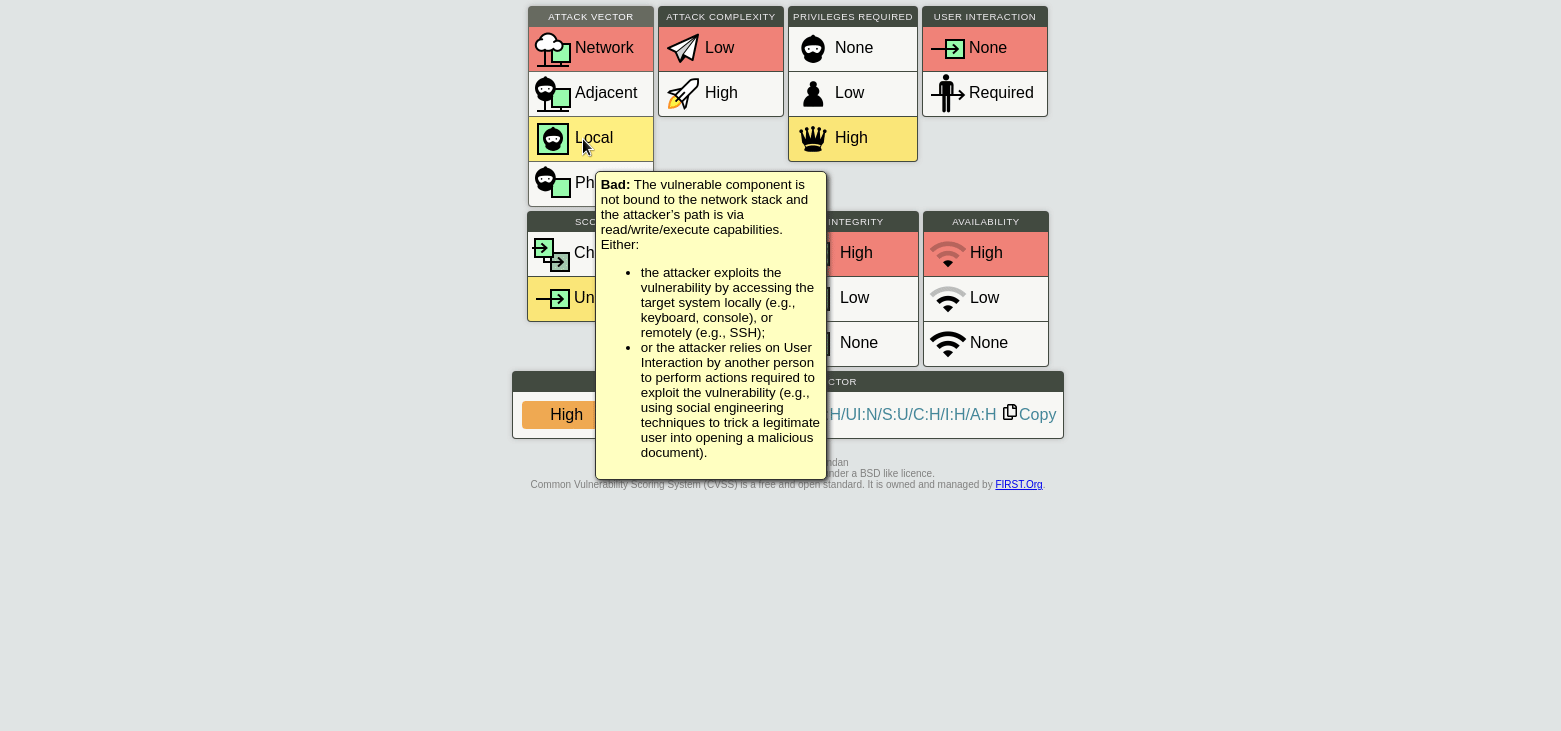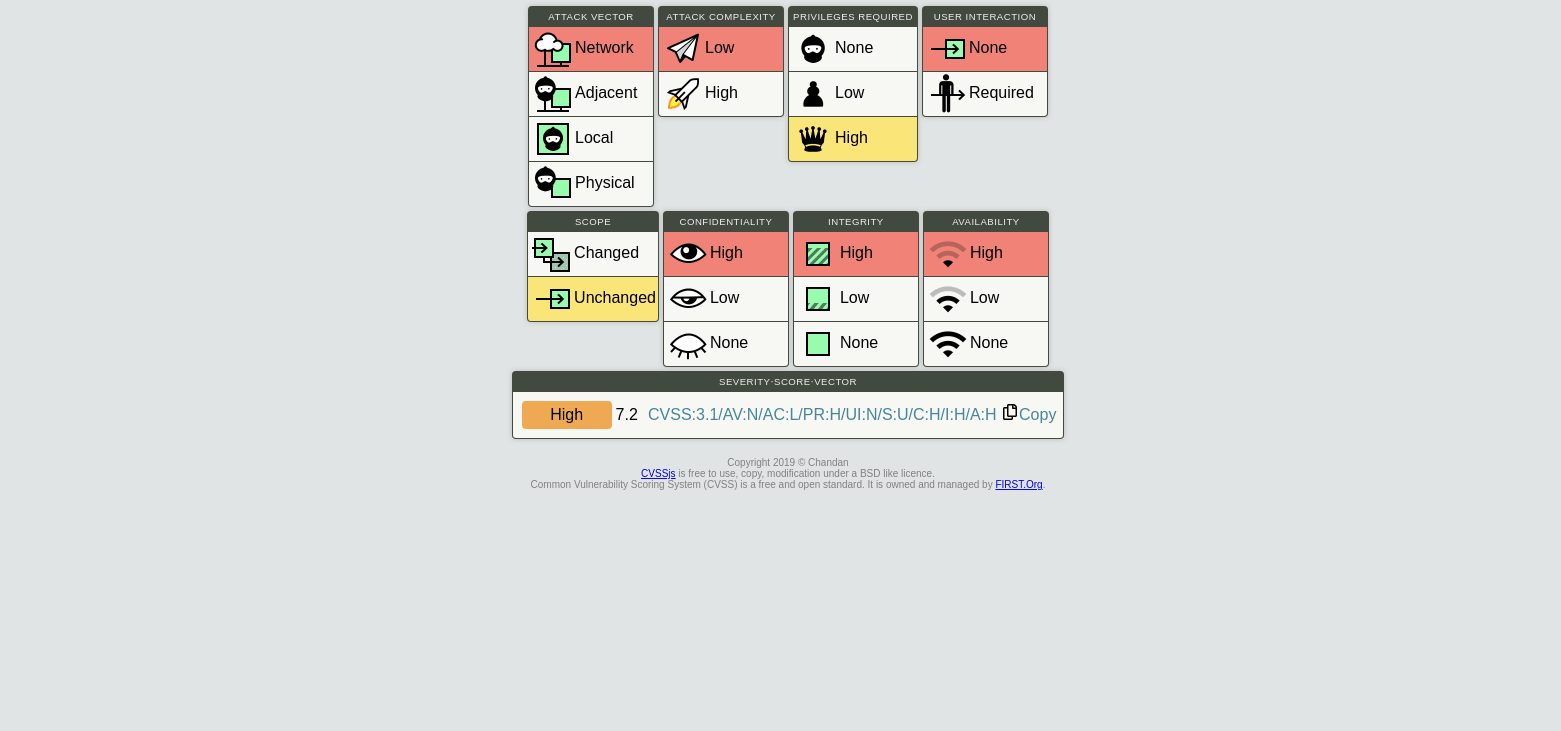
Exploit warnings
Known exploits are highlighted and linked to so you can examine the exploit quickly.
CVSS Score
All official details are listed for each CVE - with convenient links to CVSSjs.org to quickly deduce and understand the CVSS score for each vulnerability.
Copy vulnerability lists and summaries
Copy lists of vulnerabilities and product summaries and paste them into another application, i.e. into a spreadsheet.
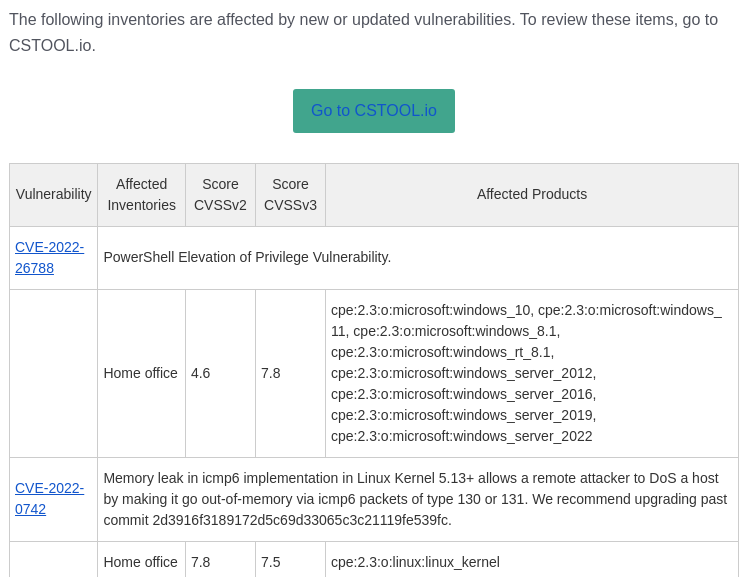
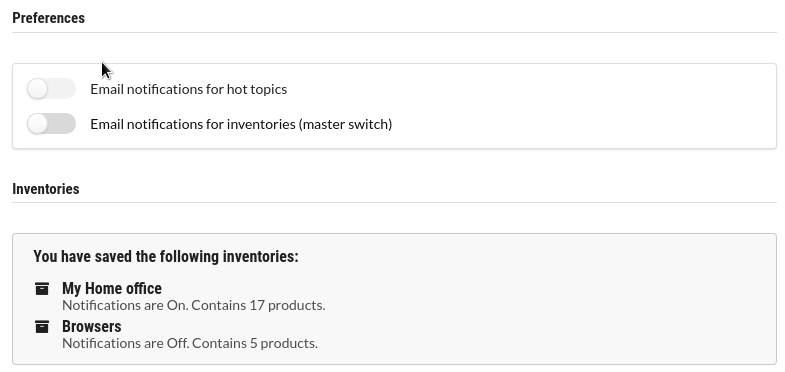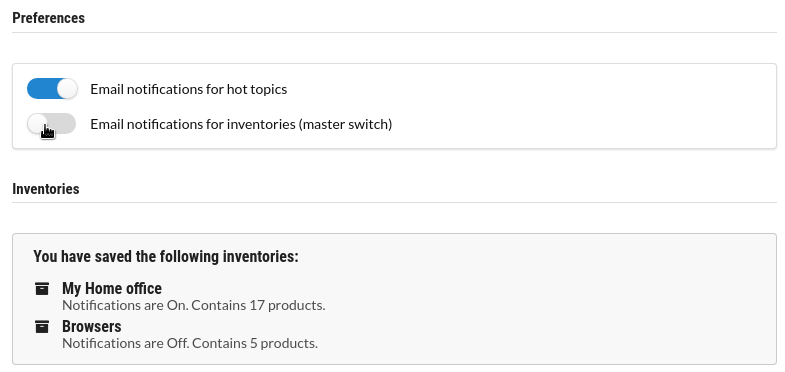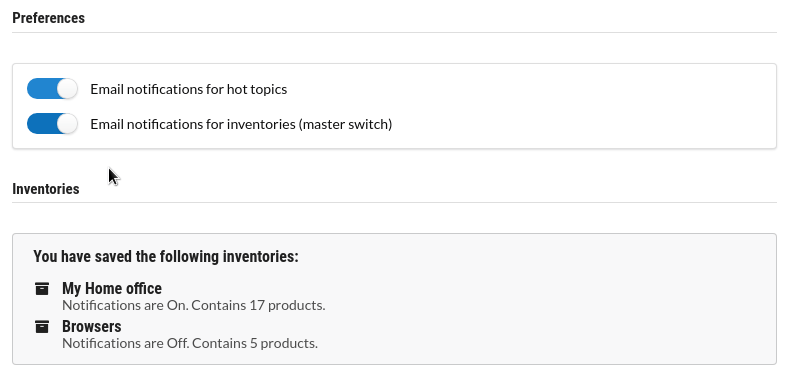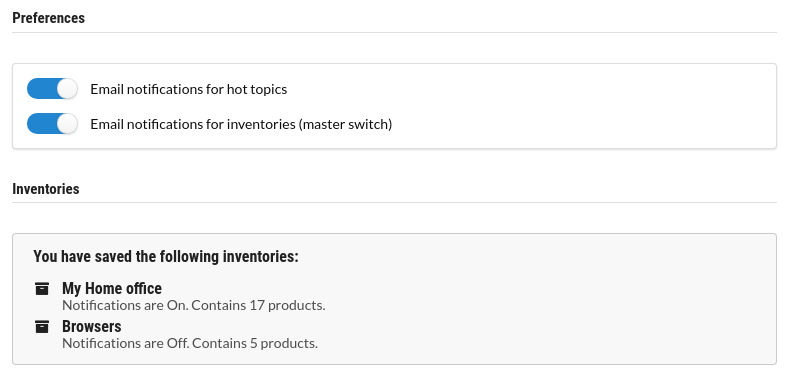
Email notifications for your inventories
Receive curated personalized emails daily for each of your inventories with newly discovered vulnerabilities.
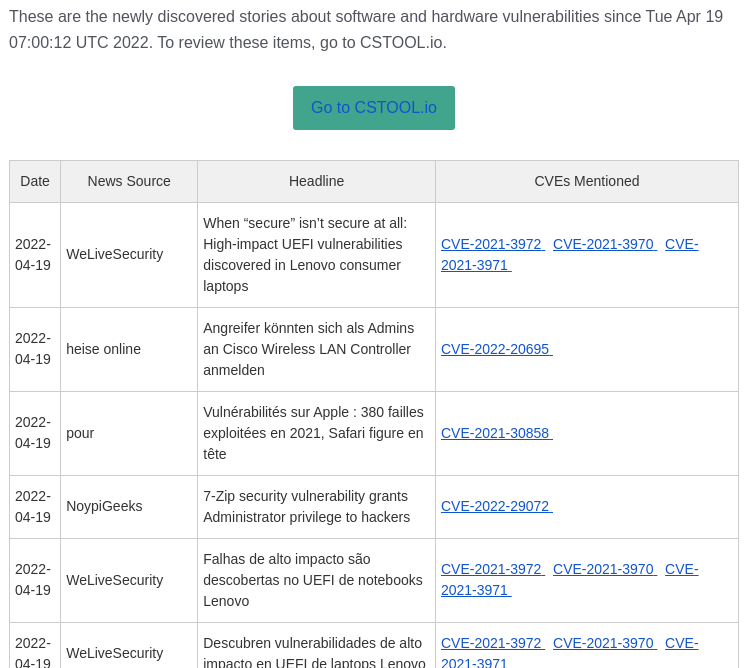
Email notifications for daily news
Get daily summaries of "hot topics" - vulnerabilities that are currently seeing coverage in the news.
Sign up with your email, Google or Github acconts
If you want to save inventories or receive emails, you may sign up with email/password or use your existing Github or Google account.
Manage inventories of products
Create your own lists of hardware and software products to get vulnerability summaries. CSTOOL.io will also monitor them for newly discovered vulnerabilities.
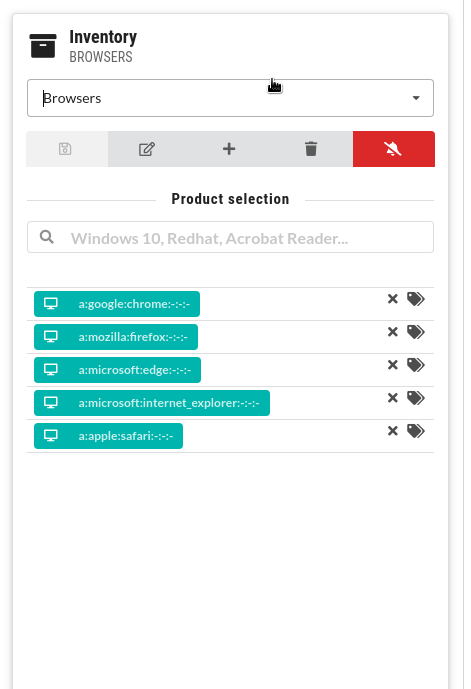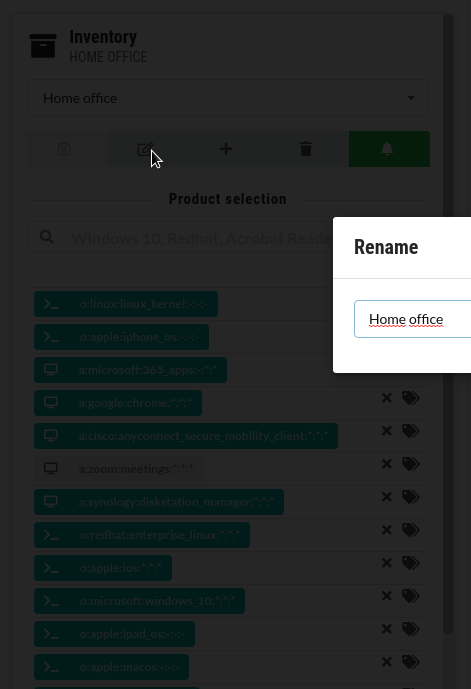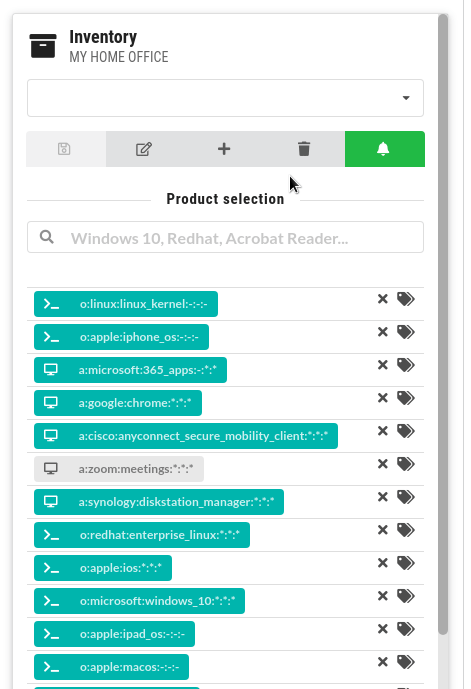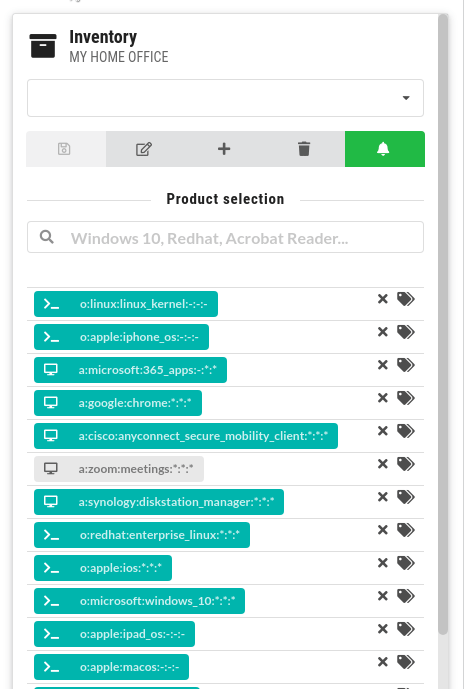
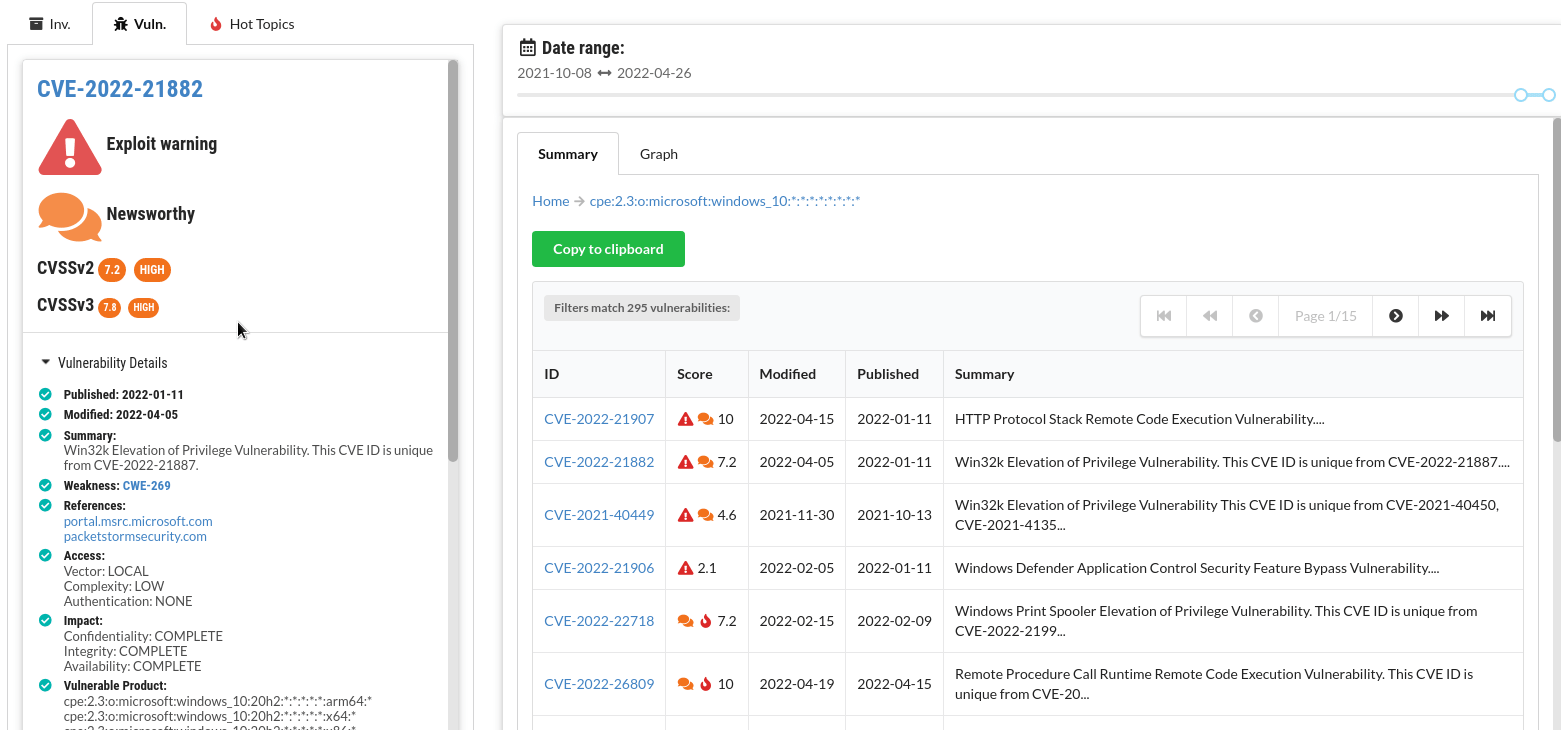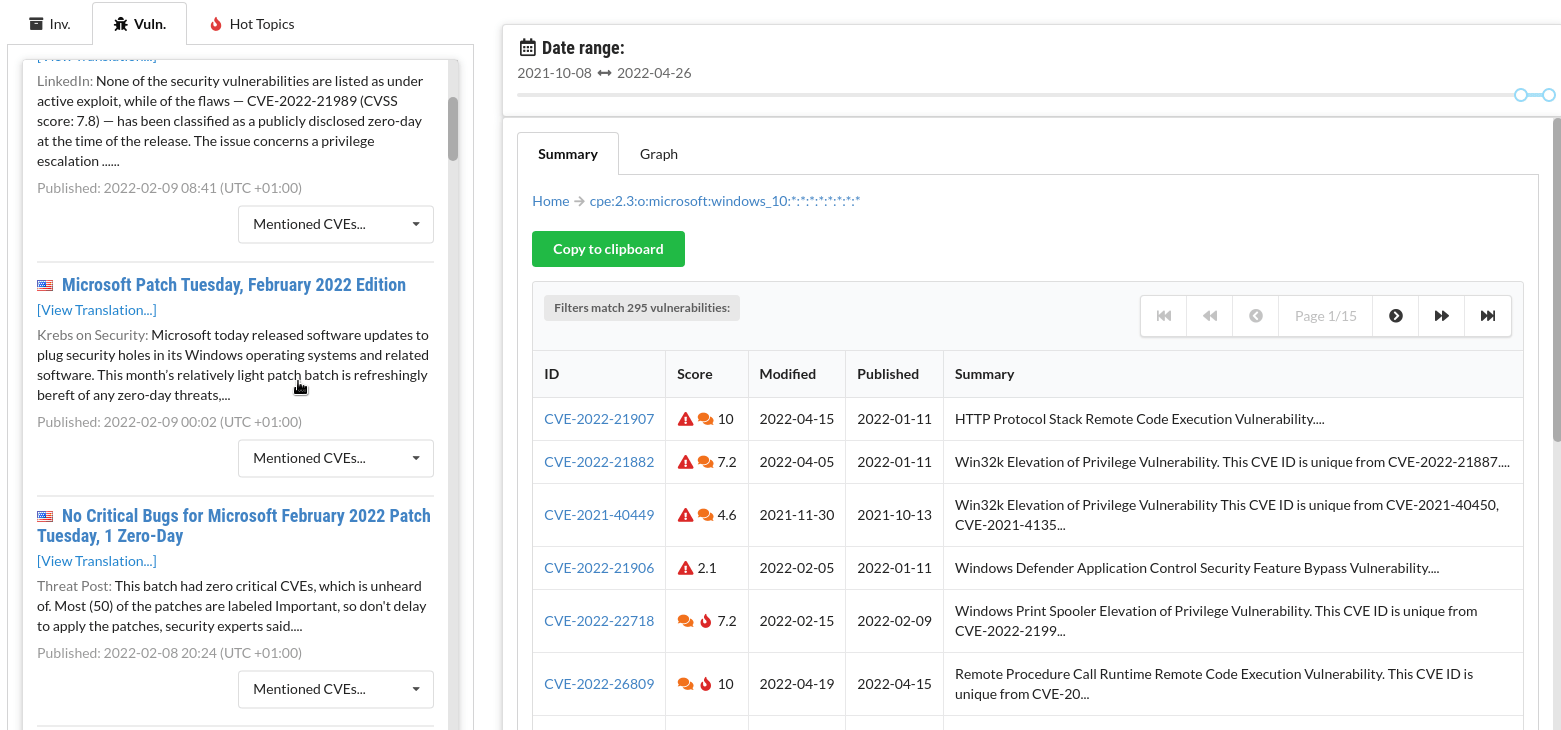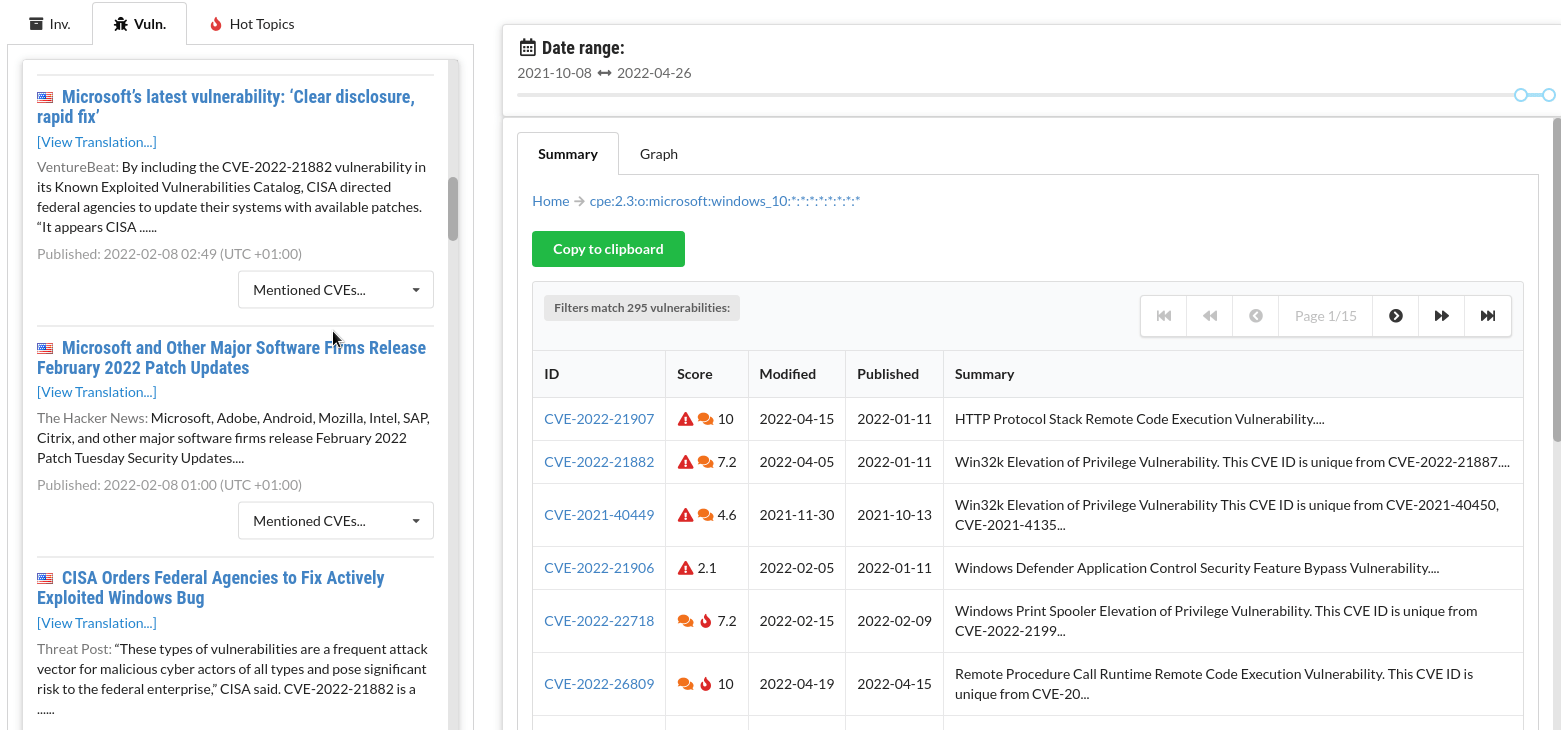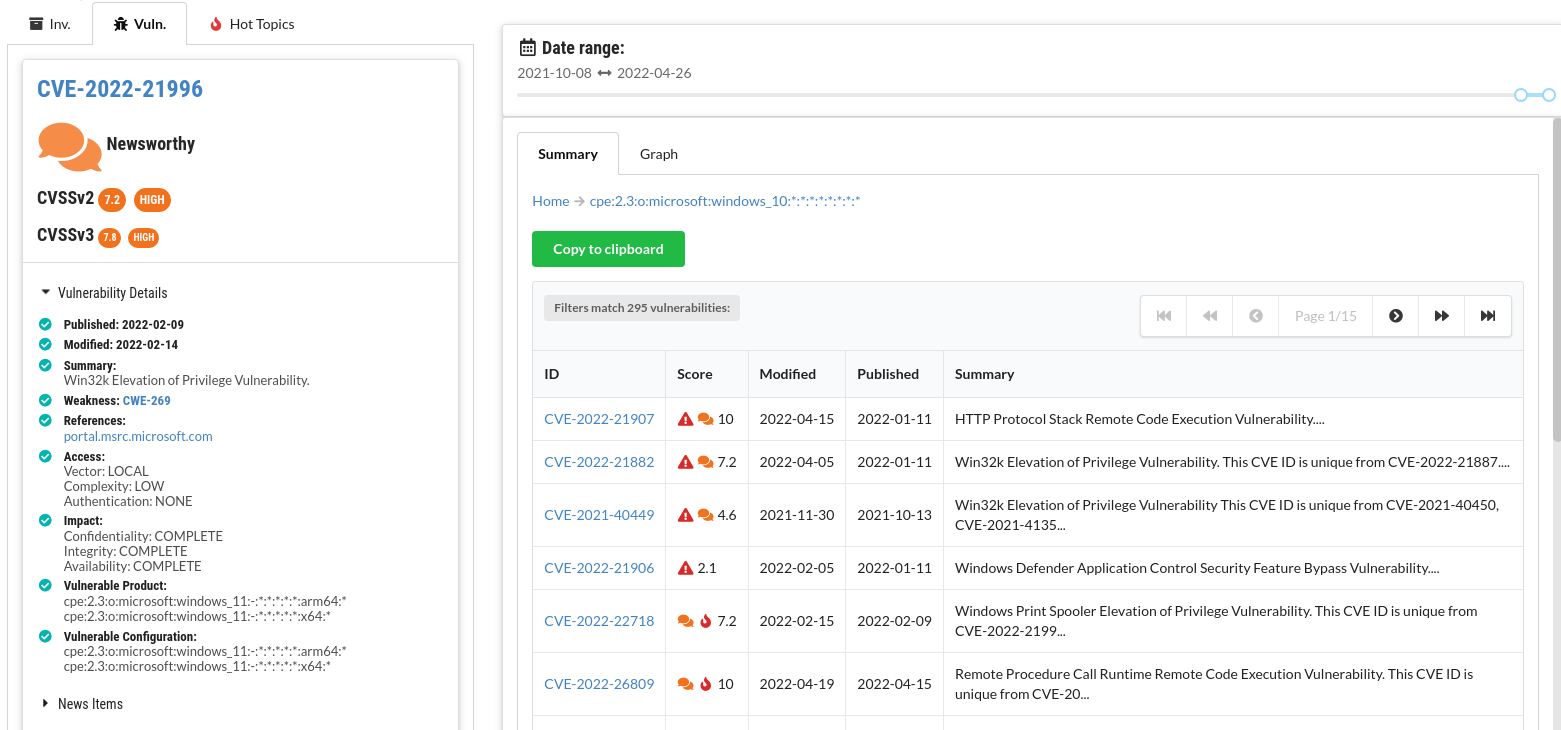
News listings for each CVE
For each vulnerability, see a list of news articles that it was mentioned in. For each article, see which other CVEs were mentioned in the same article.
Preferences
Adjust your email preferences and other settings when you have signed up with an account.

API example: Search for products
Search known vulnerabilities for software / hardware:
API Example: Search by time range
Run a search to list all vulnerabilities (and news) for the linux kernel from 2020-2022:
This is useful if you don't know the exact version(s) of software being used or if you want to
compare the vulnerability situation of multiple products (i.e. Chrome vs. Firefox). Also check out the UI to do stuff like this. Just click on any of the
nice blue buttons on this page to run the UI.
-X POST \
--data-raw '{ "vulnerableCpes":["cpe:2.3:o:linux:linux_kernel"], \
"itemsPerPage":20, \
"requestedPage":1, \
"fields":["id","cvss","references","Modified","Published","summary","has_exploit","latestNews"],\
"published":{"from":"2020-01-01T00:00:00.000Z","until":"2022-01-01T00:00:00.000Z"} }'


API Example: Search news articles for a specific CVE
Search all published news articles about a specific CVE. For new CVEs this often delivers results even if no official details have been published yet:
What is this all about?
Software has bugs. Bugs are bad. Bugs cause vulnerabilities. Attackers exploit these vulnerabilities to compromise your systems. Installing updates solves the problem - some of the time. Sometimes you cannot install an update because of existing software dependencies. Sometimes there is no update: zero-day vulnerabilities can exist for weeks until mitigation becomes possible. CSTOOL.io will help you to know which vulnerabilities are most relevant for you and decide what to do about them. This short video explains what CVEs are and how they help you to secure your systems. Watch the video or start a user-friendly interface right now:
